Latest Posts
Is Your Computer Running Slow?
Restart Your Computer
It might sound too simple, but a fresh start often clears out temporary glitches and processes that might be hogging your computer’s resources.
- Click on the Start Menu (usually the Windows icon in the bottom-left corner or center of the taskbar).
- Click the Power icon.
- Select Restart.
- Wait for your computer to completely shut down and then boot back up.
Why it helps: Restarting closes all open programs and clears your computer’s short-term memory (RAM), giving it a clean slate.
Close Unnecessary Programs and Browser Tabs
Every program and browser tab you have open uses a portion of your computer’s memory and processing power. Too many can slow things down considerably.
- Look at your Taskbar (the strip at the bottom of your screen). Are there programs open that you’re not actively using? Right-click on their icons and select Close window or Exit.
- Check your web browser (Chrome, Firefox, Edge, etc.). Do you have dozens of tabs open? Close any that you don’t immediately need.
Why it helps: Freeing up RAM and CPU cycles allows your computer to focus on the tasks you are actively performing.
Still Experiencing Slowdowns?
If you’ve followed these steps and your computer is still struggling, it might be time for a deeper look. There could be other factors at play, so its time to you call up M Cubed to take a more thorough look. We will be more than happy to see whats going on and get you’re computer back running fast as ever!
Decisions Powered by AI?
Artificial intelligence is poised to revolutionize business decision-making by enhancing speed, accuracy, and strategic foresight. As AI systems become more sophisticated, they are increasingly capable of analyzing vast datasets, identifying patterns, and generating actionable insights in real time. This shift will empower organizations to make faster, data-driven decisions, reduce human error, and uncover opportunities that might otherwise go unnoticed. By 2027, experts predict that up to half of all business decisions will be either augmented or fully automated by AI agents. However, this transformation also demands a new level of digital literacy among executives and robust governance frameworks to manage risks such as bias, data integrity, and ethical use. Businesses that invest early in AI literacy and infrastructure are likely to gain a significant competitive edge in the evolving digital economy.
Accessing Shared Mailboxes in New Outlook
Bill Brown
Did your Outlook update to a new and weird looking version of Outlook? Are you looking for your other inbox (mailbox) or perhaps your shared folders? If your Outlook looks like the new Outlook shown below, we can help!

If your email looks like the above, then the next image of Outlook will certainly help. To find those shared mailboxes or folders that have been shared with you in this new version of Outlook you’ll want to look for “Shared with me” in the left-hand navigation pane. This will be located towards the bottom of the window when you scroll down. See the image below.
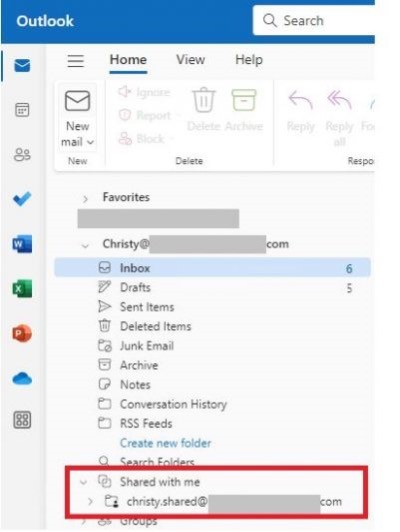
After clicking on the “Shared with me” you should now see your shared mailboxes and other shared folders that have been shared with you. If your still unable to find it or have questions reach out to our M Cubed Team and we can help with your questions about the new Outlook.
Employee Spotlight
JAMES TABOR
James finds his greatest enjoyment in creating, playing, and listening to music. Interestingly, he grows and harvests a variety of hot peppers! His motivation stems from the fear of failure, and his proudest accomplishment is being a good father. James lives by the mantra: “If you want to be good at anything you must work at it, practice creates perfection.”
5 Essential Computer Habits Every User Should Know
James Tabor
In today’s digital age, where technology is an integral part of our daily lives, understanding good computer habits is crucial for a smooth and secure user experience. Whether you’re a casual user or rely on your computer for work, adopting these habits will not only enhance your productivity but also protect your valuable data. Here are five essential computer habits every user should know:
- Regular Software Updates: Keeping your operating system, applications, and antivirus software up to date is paramount. Updates often include patches for security vulnerabilities and performance enhancements. Set your system to automatically update software whenever possible, or manually check for updates regularly.
- Strong Password Management: Your passwords are the keys to your digital kingdom. Create strong, unique passwords for each account, incorporating a mix of uppercase and lowercase letters, numbers, and symbols. Consider using a reputable password manager to securely store and manage your passwords.
- Backup Your Data: Data loss can occur due to hardware failure, malware, or human error. Regularly back up your important files and documents to an external hard drive, cloud storage service, or both. This ensures that even if something goes wrong with your computer, your data remains safe and accessible.
- Practice Safe Browsing: Exercise caution when browsing the internet. Avoid clicking on suspicious links or downloading files from unknown sources, as they may contain malware or phishing attempts. Use reputable antivirus software and enable browser security features like popup blockers and safe browsing modes.
- Be Mindful of Email Security: Email is a common vector for cyber threats such as phishing scams and malware distribution. Be cautious when opening email attachments or clicking on links, especially if they’re from unfamiliar senders or seem suspicious. Verify the legitimacy of emails before taking any action and avoid sharing sensitive information via email whenever possible.
By incorporating these five computer habits into your routine, you can significantly reduce the risk of security breaches, data loss, and other common computer-related issues. Remember, proactive measures such as regular updates, strong passwords, backups, safe browsing, and email security are essential pillars of a secure and productive computing experience. By staying informed and practicing these habits diligently, you’ll be better equipped to navigate the digital landscape safely and effectively.
Safely Handle Email Attachments and Links
Isaac Hull
- Verify the sender
Before opening any attachments or clicking a link, verify the senders email address. If the email address is suspicious or looks unfamiliar, reach out to the sender via a known contact method to confirm its legitimacy. - Don’t Open Unexpected Attachments
Even if an email looks legitimate, if you weren’t expecting an attachment, don’t open it. If you were expecting an email but are unsure whether an attachment was to be sent, reach out to the sender and confirm they meant to send an attachment. - Hover Over Links
Before clicking a link in an email (or mostly anywhere), you can hover your cursor over the link to see the URL. Most apps also show a small preview of what the website looks like. With this information, you can determine whether the link is safe to click. - When in Doubt, Delete
If you have any uncertainty with an email and you are unable to verify its legitimacy, it is best to be cautious and delete it. It will always be safer to miss an email than risk compromising you or your company’s data.
SLAM Method: Protecting Your Business from Phishing Attacks
Jeff Sterling
There is a reason why phishing is usually at the top of the list for security awareness training. For the last decade or two, it has been the main delivery method for all types of attacks. Ransomware, credential theft, database breaches, and more can be launched via a phishing email.
Why has phishing remained such a large threat for so long? Because it continues to work. Scammers evolve their methods as technology progresses. They use AI-based tactics to make targeted phishing more efficient, for example.
If phishing didn’t continue working, then scammers would move on to another type of attack. But that hasn’t been the case. People continue to get tricked. They open malicious file attachments, click on dangerous links, and reveal passwords.
Studies also show that as soon as 6 months after training, phishing detection skills wane. Employees begin forgetting what they’ve learned, and cybersecurity suffers as a result.
Give your employees/coworkers an easy to remember method for suspicious of phishing identification – SLAM!
Phishing: A cyber-attack tricking individuals into revealing sensitive information such as passwords, client data, financial data, or for the unsuspecting user to download an attachment or visit a link to infect their computer, usually via email.
Types of Phishing: Includes social engineering methods like smishing (texts) and vishing (calls).
SLAM Acronym:
- Sender: Verify the sender’s email address.
- Links: Check where links lead.
- Attachments: Be cautious with file attachments.
- Message: Assess if the email makes sense.
Best Practices:
- Teach the SLAM method or implement Security Awareness Training (SAT).
- Use business-grade endpoint & anti-virus protection.
- Scan files sources, services and malware to secure document sharing.
- Implement Zero Trust Cyber Security.
Understanding and using SLAM can help prevent phishing, a leading cause of data breaches. Both awareness training and security software can improve your defenses against phishing attacks. Contact us today to discuss your email security needs.
Thank you
Dear Valued Clients,
As this year is wrapping up, we always like to reflect on everything we have accomplished and how we would not be successful without every one of you. On behalf of everyone at M Cubed Technologies, we want to express our deepest gratitude for your partnership. We realize how lucky we are to have all of you entrust us with your IT needs. That partnership is not taken lightly, and we are honored to be a part of your success story.
We appreciate your willingness to work with us and our staff. We realize that this isn’t a one-way road, but a collaborative effort. Your feedback and communication are very important to us, and it allows us to deliver the best quality service to you and your employees. As the new year is quickly approaching, we look forward to working with you in supporting your goals and building on the strong foundation we have established.
Thank you so much for your loyalty and support!
M Cubed Family
Dangers of Browser Extensions
Joe Ryan
Browser extensions can be incredibly useful, but they also pose significant risks if not carefully managed. Malicious extensions can lead to security breaches, performance issues, and even legal problems. These extensions often request extensive permissions, potentially allowing them to harvest your data without your knowledge or consent. Installing an unknown extension can be a gateway for malware or spyware, secretly accessing sensitive information like passwords, browser history, and banking details. In addition to security risks, malicious extensions can also slow down your device. If web pages load more slowly than usual or if your device experiences random slowdowns, it might be infected with a harmful extension. The unauthorized collection of sensitive data could lead to data mishandling, which may result in legal complications or violations. Even seemingly legitimate extensions should be approached with caution. Always research an extension before downloading it to ensure it’s trustworthy.
How to Protect Yourself
To minimize the risks posed by browser extensions:
- Review permissions before installing an extension
- Download only from trusted sources (like official browser stores).
- Regularly review and update your extensions, removing any that are unnecessary or unknown.
- Manage extensions via your browser’s extension settings (usually accessed by clicking the triple-dot menu or puzzle piece icon in the browser toolbar).
By staying vigilant, you can protect your device and personal data from potential threats.
Lawrence 10-Year Anniversary Party
2024 marks the 10 year anniversary of the opening of the Lawrence, Kansas location of M Cubed. Thank you to all of our clients, friends, and supporters who were able to come out and celebrate this milestone. Here is to another 10 years!
The Importance of Employee Cyber Awareness Training
IT departments and CTO’s can spend tireless hours developing strategies and implementing policies and hardware that will help prevent future cyber incidents. These incidents can cripple and outright destroy organizations. Cybercrime is a multi-trillion-dollar industry that everyone fears yet does not discuss enough. One of the best ways to prevent a critical cyber incident is to educate your employees.
96% of all cyber attacks began with an end user clicking on a malicious attachment in an email or visiting a site that had malicious content. By educating people on how to operate cautiously through this ever-growing environment, organizations can greatly lower their exposure and therefore decrease the risk of a critical cyber event. M includes cyber awareness training for all our clients on a bi-annual basis. Contact your Account Manager today to schedule your company’s next cyber awareness class.
Phishing Awareness Training
MCubed will simulate phishing attacks on your end users and provide comprehensive reporting and training for those who take the bait.
How often should you reboot your router?
In general, it’s advisable to restart your router about once a month, especially for home and small Business networks. This practice helps maintain peak performance by clearing stored memory and fixing minor connectivity issues. Many routers offer options to schedule automatic reboots through their app or web interface. This feature allows you to set a convenient time each month, like overnight when internet usage is minimal, ensuring uninterrupted service.
Windows 10 End Of Life
Microsoft has announced that Windows 10 will reach its end of life in October 2025. As a result, MCubed account managers will be contacting clients to discuss upgrading their machines. They will focus on replacing or upgrading eligible machines from Windows 10 to Windows 11, ensuring a smooth transition to a more secure and up-to-date operating system. This effort aims to maintain the efficiency of clients’ IT infrastructure.
City of Fresno Loses $600,000.00 To Phishing Scam
Hackers pretending to be a construction company hired by the City of Fresno to build a new police department convinced two city accountants to transfer $600,000.00 to them. To prevent this from happening to you, contact M Cubed for more information.
If you would like to continue reading on how this happened to the City of Fresno, visit The Fresno Bee article here.
How to Avoid Phishing Scams
Pete James
Phishing scams are a persistent threat because they are profitable for cybercriminals. To protect yourself, follow these guidelines:
- Stay Informed: Keep up with new phishing techniques and conduct regular security awareness training.
- Think Before You Click: Avoid clicking on links in random emails; hover to verify links first.
- Use Anti-Phishing Toolbars: Install these in your browser for an extra layer of protection.
- Verify Site Security: Look for “https” and a lock icon before submitting sensitive information.
- Check Accounts Regularly: Monitor your online accounts and bank statements for suspicious activity.
- Update Your Browser: Install security patches promptly to close vulnerabilities.
- Use Firewalls: Employ both desktop and network firewalls to block intrusions.
- Beware of Pop-Ups: Block or close pop-ups, avoiding any action buttons within them.
- Protect Personal Information: Never share sensitive information through links in emails.
- Install Antivirus Software: Keep it updated to guard against the latest threats.
By following these steps, you can make sure you aren’t the one getting the company breached!
Windows 10 End of Life October 14th, 2025
Windows 10 is nearing the end of support by Microsoft. The official date for this is October 14th, 2025. At that time Microsoft will no longer be releasing crucial updates and security patches for that operating system. This will in turn become a massive security risk for organizations and individuals.
Windows 11 will become the new standard, and M Cubed Account Managers will be contacting you to start this transition. Some computers will have the option to be upgraded at no cost to users, though some computers will not have the processing power to be upgraded and will need to be replaced. Feel free to contact your Account Manager if you would like to get a jump start on this process.
Are you having trouble with a website?
Martin Arrechavaleta
Have you ever ran across a website that is not displaying items properly, saying you are logged in even though you logged out 30 minutes ago or any other general issue? Most issues with websites can be solved by clearing the cookies and cache of the website. Clearing these are a bit different in every browser but the steps for the most popular browsers are below.
- Chrome: Press Ctrl + H on your keyboard, Click on the “Clear browsing data” tab on the left, Make sure “all time” is selected in the time range drop down menu and make sure that the cookies and other site data and the cached images and files checkbox are selected then press on the clear data button.
- Edge: Press Ctrl + H on your keyboard, Click on the three dots in the menu that opened followed by “Open History Page”. You will then click on the “Clear browsing data” button. Make sure “all time” is set in the time range drop down box, the cookies and other site data and cached images and files checkbox are selected then press on the clear now button.
- Firefox: Click on the menu button on the top right of the browser page and click on history. You will then click on “clear recent history”. Ensure the Time range drop down menu is set to “Everything”. Ensure the cookies and cache check box are set then press on the “Clear now” button.
After this is done it is recommended to restart the browser, including all tabs that might be open, not just the website that is giving you trouble. If the website is still giving you trouble feel free to give us a call and we can dig in deeper.
5 Essential Computer Habits Every User Should Know
James Tabor
In today’s digital age, where technology is an integral part of our daily lives, understanding good computer habits is crucial for a smooth and secure user experience. Whether you’re a casual user or rely on your computer for work, adopting these habits will not only enhance your
productivity but also protect your valuable data. Here are five essential computer habits every user should know:
- Regular Software Updates: Keeping your operating system, applications, and antivirus software up to date is paramount. Updates often include patches for security vulnerabilities and performance enhancements. Set your system to automatically update software whenever possible, or manually check for updates regularly.
- Strong Password Management: Your passwords are the keys to your digital kingdom. Create strong, unique passwords for each account, incorporating a mix of uppercase and lowercase letters, numbers, and symbols. Consider using a reputable password manager to securely store and manage your passwords.
- Backup Your Data: Data loss can occur due to hardware failure, malware, or human error. Regularly back up your important files and documents to an external hard drive, cloud storage service, or both. This ensures that even if something goes wrong with your computer, your data remains safe and accessible.
- Practice Safe Browsing: Exercise caution when browsing the internet. Avoid clicking on suspicious links or downloading files from unknown sources, as they may contain malware or phishing attempts. Use reputable antivirus software and enable browser security features like popup blockers and safe browsing modes.
- Be Mindful of Email Security: Email is a common vector for cyber threats such as phishing scams and malware distribution. Be cautious when opening email attachments or clicking on links, especially if they’re from unfamiliar senders or seem suspicious. Verify the legitimacy of emails before taking any action and avoid sharing sensitive information via email whenever possible.
By incorporating these five computer habits into your routine, you can significantly reduce the risk of security breaches, data loss, and other common computer-related issues. Remember, proactive measures such as regular updates, strong passwords, backups, safe browsing, and email security are essential pillars of a secure and productive computing experience. By staying informed and practicing these habits diligently, you’ll be better equipped to navigate the digital landscape safely and effectively.
Protecting Yourself From Scams
Megan Downum
Every day you get flooded with emails, but how do you tell if one is really from your boss or the bank? Scam emails are becoming an everyday occurrence, and no matter how much spam filtering you have, scammers are always going to be one step ahead and things are always going to get through. Below are two steps to help you navigate being able to differentiate scam emails versus legitimate emails:
- Senders Email: Anyone can open a new email address and say their name is your boss, a colleague, or even use your name. What they often cannot do though is to mimic the actual email address. When you see an email, after the sender’s name, the email address is listed in <>.
Example: From: Mr. Big Bossman
When looking at emails, especially ones that may seem a little off, make sure you check the actual email address they are sending from, not just the name. - Always double check requests: Scam emails almost always contain a request, whether that be something like buying Amazon gift cards and sending the scammer the codes, to changing banking information, to logging into fake sites to gain your credentials. If the request is not something you were suspecting, reach out directly to whoever you believe sent the request. Do not reply to the email, but start a fresh new email, or call the person in question. If an email is asking you to log in somewhere because your account was compromised, reach out to the account or sign in without following the link in the email.
Not sure? That’s why we are here! Scammers get smarter and better every day. But do you know what they don’t have? M Cubed! We are here for you 24-7 if you ever need us to check an email. We are trained in spotting spam and can even test links to check and see if they are valid or not. Feel free to forward our team any emails you are not sure about, and we can let you know if they are safe or not.
Your Greatest Cyber Security Risk May Surprise You
Jesse Gibson
When it comes to cyber security, employees are a company’s greatest asset while simultaneously being their greatest risk. This is why at M Cubed we are strong proponents of doing continued education on cyber security. We want to provide your staff with the knowledge to spot a phishing email or a risky website. While these training courses are incredibly valuable, we believe they are the bare minimum. How do you know the knowledge is being retained? Maybe a user is in the middle of a busy day and has a lapse in judgment or is simply moving too fast. How do you help correct or even identify these behaviors and drive home the importance of being safe online?
The simple answer to these questions is to try and hack them! Running a phishing campaign against your staff is a great and easy way to identify where your security flaws exist at the user level. It is also a great way to empower your employees with useful knowledge that not only applies to their work life, but also their home life. Essentially, we try and entice end users to click on links and input sensitive information. If a user does this then they are directed to watch a short video on cyber security and take a quick test. By running these campaigns across a yearlong period, it makes your staff stay much more alert and they are much less likely to have cyber security incidents. This type of training is becoming more and more prevalent and is even being required by some cyber liability insurance carriers. If you are interested in learning more, please feel free to reach out to us and we can set up a custom campaign just for your business.
Passwords 101
Logan Cerutti
In today’s online world, keeping your accounts safe with strong passwords is super important. We’re here to give you some easy tips to help you create and manage your passwords better. First off, make sure your passwords are long and complicated, using a mix of letters, numbers, and symbols. Avoid using things that are easy to guess, like your birthday or your pet’s name. And it’s a good idea to use different passwords for each of your accounts just in case one of them becomes compromised.
If remembering lots of different passwords sounds tricky, don’t worry! There are tools called password managers that can help. They keep your passwords safe and can even make strong passwords for you. At M Cubed Technologies, we’re all about keeping you safe online. If you ever need a hand with your passwords or anything else tech-related, just give us a shout. Let’s work together to keep your accounts safe and your information secure.
Why You Need to Reboot
Written by Chad Sinclair
Imagine your computer as a busy workspace. Throughout the day, programs pile up like papers, temporary files linger like coffee mugs, and background processes hum like forgotten printers. No wonder things get sluggish by morning! That’s why a daily restart is like a magic reset button. It sweeps away those digital leftovers, freeing up memory and resources.
M Cubed schedules a restart to your computer once a week, like a weekly housekeeper, making sure your computer gets any updates, but if you notice your computer is running a little sluggish, give it a restart! It’s just a few minutes for a smoother, faster, and more secure morning – like starting your day with a tidy desk and a fresh cup of coffee!
Copilot: Microsoft’s new 365 AI Assistant

Get ready to ditch the tedious tasks and embrace lightning speed with Microsoft’s game-changing AI Assistant, Copilot, now available to ALL 365 users! Imagine:
- Effortless Document Creation: Brainstorm killer content, breeze through edits, and craft emails that resonate – all with Copilot’s intelligent guidance at your side.
- Streamlined Workflows: Eliminate repetitive tasks and automate complex processes across Word, Excel, PowerPoint, Outlook, and more. Focus on what matters most, while Copilot handles the heavy lifting.
- Time-Saving Efficiency: Cut your workload in half! Copilot anticipates your needs, suggests intelligent solutions, and helps you achieve more in less time.
- Unmatched Personalization: Copilot learns your unique style and preferences, adapting its assistance to deliver a truly seamless experience.
Ready to unlock the power of Copilot? Contact your Account Manager today to discuss implementation today!
Is your device at risk?
Written by Bill Brown
A second layer of security can protect against common hacker attacks.
MFA works by providing a 2nd layer of security in the form of sending you a code via an authentication application such as Google Authenticator or Microsoft Authenticator and even by text message. Now you might be asking yourself how hackers bypass this if they aren’t being sent the code or don’t have access to the authenticator app. This is where we come across a term used in the security industry called MFA Fatigue. MFA Fatigue is caused by sending a request for an MFA code being sent to a user so many times that they eventually accept it. You probably have noticed that when we turn on MFA, we have it send you a code that requires you to put the code in or verify it with the application. MFA has another method where it just sends you a link stating something like “Hey did you recently try to sign into this site?” Those are the types that generally fall into the category of being able to be cracked by MFA Fatigue.
Difficulty Reading Text in Your Web Browser?
Written by Anthony Choza
You can quickly change the text size of any web page by taking these easy steps.
Finding it hard to read text in your web browser? You can quickly change text size of any web page by holding down Ctrl and the mouse wheel up or down OR Ctrl and +/-. This will also work on your desktop to change the size of your desktop icons and the icons in your folders.


